iCMS v8.0.0 Reflected Cross-Site Scripting (XSS) Vulnerability Report

iCMS v8.0.0 Reflected Cross-Site Scripting (XSS) Vulnerability Report
1. Vulnerability Overview
- Product: iCMS
- Version: v8.0.0
- Vulnerability Type: Reflected Cross-Site Scripting (XSS)
- Affected Component: User Management Module (
app/user/views/index.html) - Parameter:
regip,loginip - Discoverer: [Your Name/Handle]
2. Vulnerability Description
iCMS v8.0.0 contains a Reflected Cross-Site Scripting (XSS) vulnerability in the User Management component. The application directly echoes the regip and loginip GET parameters into the HTML value attribute without proper sanitization or escaping. This allows remote attackers to execute arbitrary web script or HTML.
3. Technical Analysis
The vulnerability is located in the file app/user/views/index.html.
Around line 43 and 49, the PHP code directly outputs the $_GET parameters into the input tag’s value attribute:
1 | <!-- app/user/views/index.html --> |
Root Cause: The developer failed to wrap $_GET['regip'] with htmlspecialchars() or a similar filtering text function before outputting it to the browser. As a result, malicious HTML/JS characters like " and > break out of the value="" attribute.
4. Proof of Concept (PoC)
To exploit this vulnerability, an attacker can append a malicious payload to the URL accessing the user list.
Payload:
1 | "><script>alert(1)</script> |
Full Exploit URL:
1 | http://<targeted-host>/admincp.php?app=user®ip="><script>alert(1)</script> |
(Note: The admincp.php path might vary depending on installation, e.g., renamed for security)
5. Reproduction Steps
Login to the iCMS administration panel.
Navigate to the User Management section.
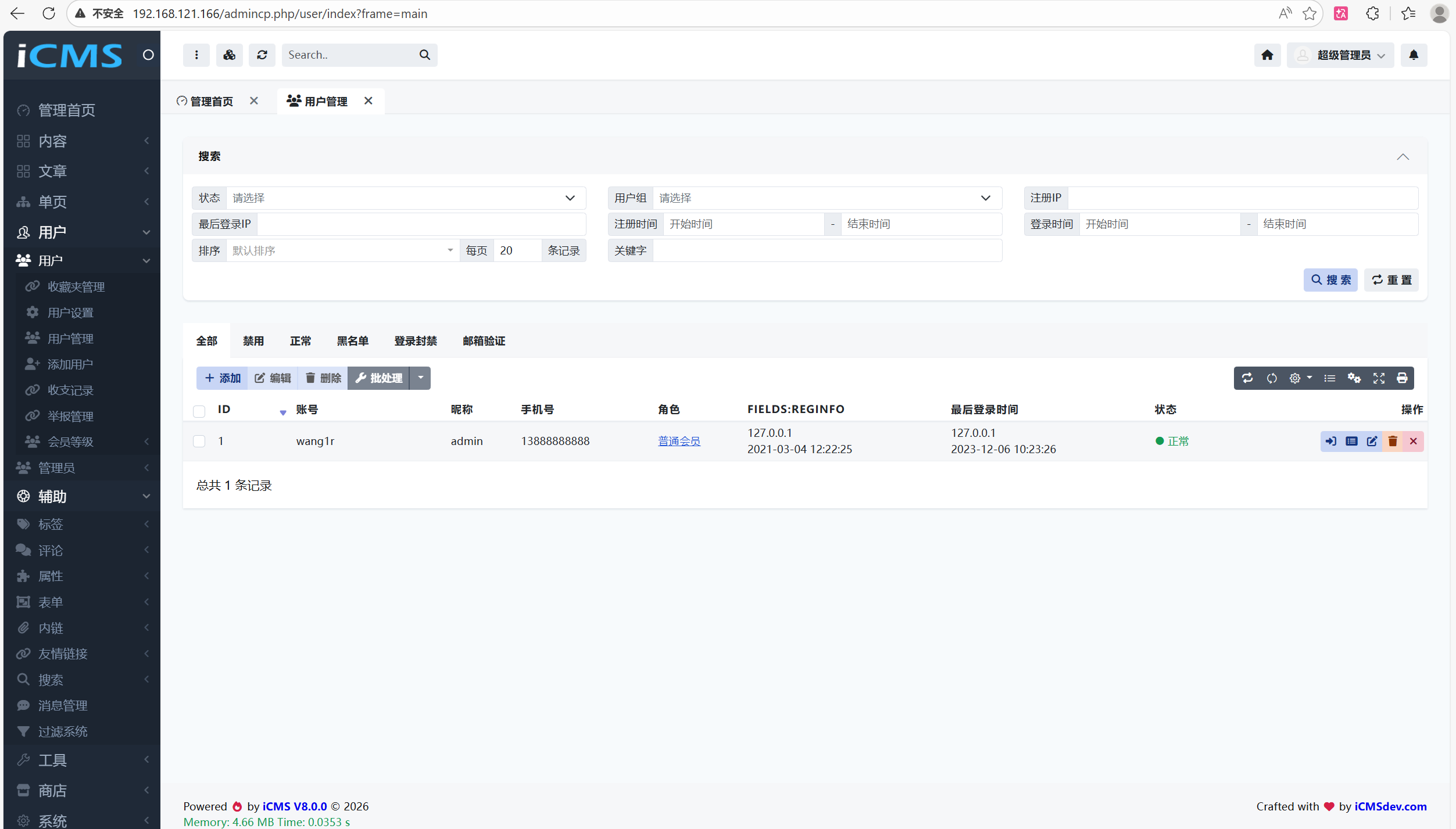
Construct the malicious URL containing the XSS payload: http://192.168.121.166/admincp.php?app=user®ip=%22%3E%3Cscript%3Ealert(1)%3C/script%3E
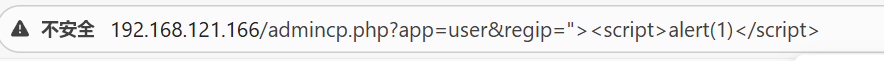
- The application reflects the payload, executing the JavaScript.
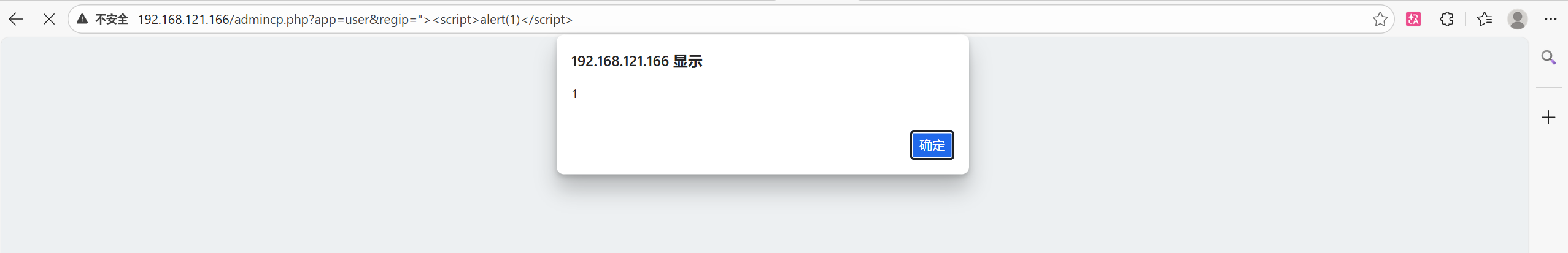
6. Impact
Attackers can use this vulnerability to:
- Redirect administrators to malicious websites.
- Perform actions on behalf of the administrator (CSRF) via JavaScript execution.
- Display phishing forms to steal credentials.
(Note: Cookie theft viadocument.cookieis mitigated by the HttpOnly flag in this version, but other XSS impacts remain valid.)
7. Recommendation
It is recommended to sanitize the input before outputting it to the view. Use htmlspecialchars() to escape special characters.
Patch Example:
1 | <!-- Fixed Code --> |
- 标题: iCMS v8.0.0 Reflected Cross-Site Scripting (XSS) Vulnerability Report
- 作者: Wang1r
- 创建于 : 2026-02-09 16:24:00
- 更新于 : 2026-02-09 20:27:17
- 链接: https://wang1rrr.github.io/2026/02/09/CVE-Report-iCMS-v8.0.0-XSS/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。